What guidance identifies federal information security controls pii? With this question at the forefront, this paragraph opens a window to an amazing start and intrigue, inviting readers to embark on a storytelling gaya akademik dengan tone otoritatif filled with unexpected twists and insights.
The content of the second paragraph that provides descriptive and clear information about the topic
Definition and Scope of PII

Personally identifiable information (PII) refers to any data that can be used to identify an individual, either directly or indirectly. Federal regulations define PII as any information that can be linked to an individual, including:
- Name
- Social Security number
- Date and place of birth
- Mother’s maiden name
- Biometric data
- Medical or health information
- Financial information
- Educational information
PII poses significant risks if it falls into the wrong hands, as it can be used for identity theft, fraud, and other malicious purposes.
Federal Information Security Controls for PII
To protect PII, federal agencies must implement a comprehensive set of information security controls. These controls are designed to prevent unauthorized access, use, disclosure, alteration, or destruction of PII.
NIST SP 800-53
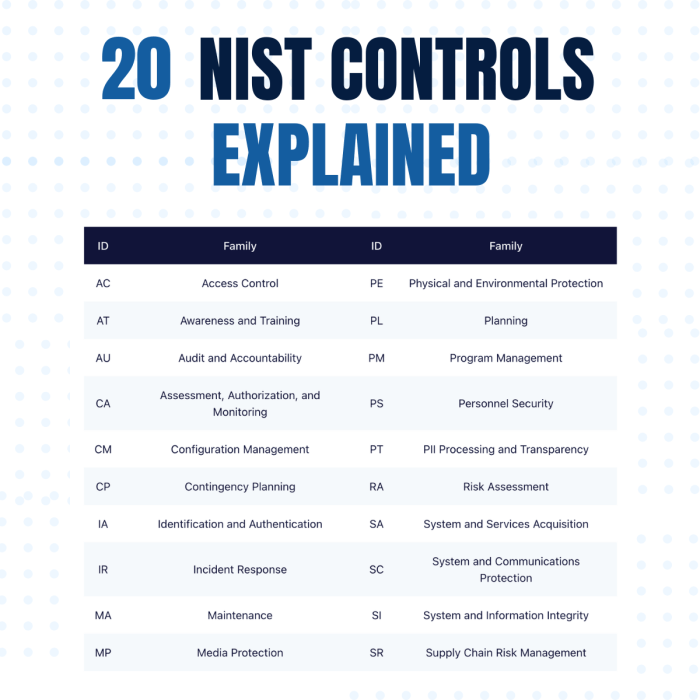
NIST SP 800-53 provides guidance on security controls for federal information systems. The controls specifically relevant to PII protection include:
- AC-2: Access Control
- IA-5: Identification and Authentication
- IA-11: Audit Trails
- SC-8: System Configuration Management
- SC-18: Incident Response
NIST SP 800-171
NIST SP 800-171 provides guidance on protecting PII in cloud computing environments. The controls specifically relevant to PII protection include:
- CM-7: Cloud Access Management
- CM-15: Data Security
- CM-18: Incident Response
- CM-25: Audit Logging
Guidance for Implementing PII Security Controls

To assist organizations in implementing PII security controls, several guidance documents have been developed.
OMB Memorandum M-17-12
OMB Memorandum M-17-12 provides guidance on protecting PII in federal agencies. It recommends that agencies:
- Develop a PII protection plan
- Implement NIST SP 800-53 and NIST SP 800-171
- Conduct regular security assessments
- Provide training to employees on PII protection
HIPAA Security Rule
The HIPAA Security Rule provides guidance on protecting PII in the healthcare industry. It requires covered entities to:
- Conduct a risk assessment
- Implement security controls to protect PII
- Provide training to employees on PII protection
Compliance with PII Security Requirements
Organizations that fail to comply with PII security requirements may face significant penalties. These penalties can include:
- Fines
- Civil lawsuits
- Criminal charges
In addition to legal penalties, non-compliance can also damage an organization’s reputation and lead to loss of customer trust.
Steps for Compliance, What guidance identifies federal information security controls pii
- Conduct a risk assessment
- Develop a PII protection plan
- Implement NIST SP 800-53 and NIST SP 800-171
- Conduct regular security assessments
- Provide training to employees on PII protection
Case Studies and Best Practices: What Guidance Identifies Federal Information Security Controls Pii
Case Study: Equifax Data Breach
In 2017, Equifax experienced a data breach that exposed the PII of over 145 million Americans. The breach was caused by a vulnerability in Equifax’s web application that allowed attackers to access sensitive data.
The Equifax data breach is a reminder of the importance of implementing strong PII security controls. Organizations should:
- Regularly patch software and systems
- Implement multi-factor authentication
- Encrypt sensitive data
- Conduct regular security assessments
Common Queries
What is PII?
Personally identifiable information (PII) refers to any data that can be used to identify an individual, such as name, address, Social Security number, or biometric data.
What federal regulations cover PII?
Various federal regulations address PII protection, including the Health Insurance Portability and Accountability Act (HIPAA), the Gramm-Leach-Bliley Act (GLBA), and the Federal Information Security Management Act (FISMA).
What are the key federal information security controls for PII?
NIST Special Publication 800-53 provides a comprehensive list of security controls specifically designed to protect PII, including access control, encryption, and incident response.
What guidance documents offer best practices for implementing PII security controls?
The National Institute of Standards and Technology (NIST) publishes several guidance documents, such as NIST Special Publication 800-122, which provide detailed recommendations for implementing PII security controls.
What are the consequences of non-compliance with PII security requirements?
Non-compliance with PII security regulations can result in significant penalties, including fines, reputational damage, and legal liabilities.